Nikon and Sony are solving the Deepfake Problem Using Digital Signatures
In December last year, Vladimir Putin, the current president of Russia spoke at the Annual Press Conference in Moscow. Towards the end of the event, he took questions via video calls from people nationwide.
As he finished answering one of the questions and moved on to the next question, he was greeted by someone special.
Himself.
Sitting in a chair across from Vladimir Putin was Vladimir Putin.
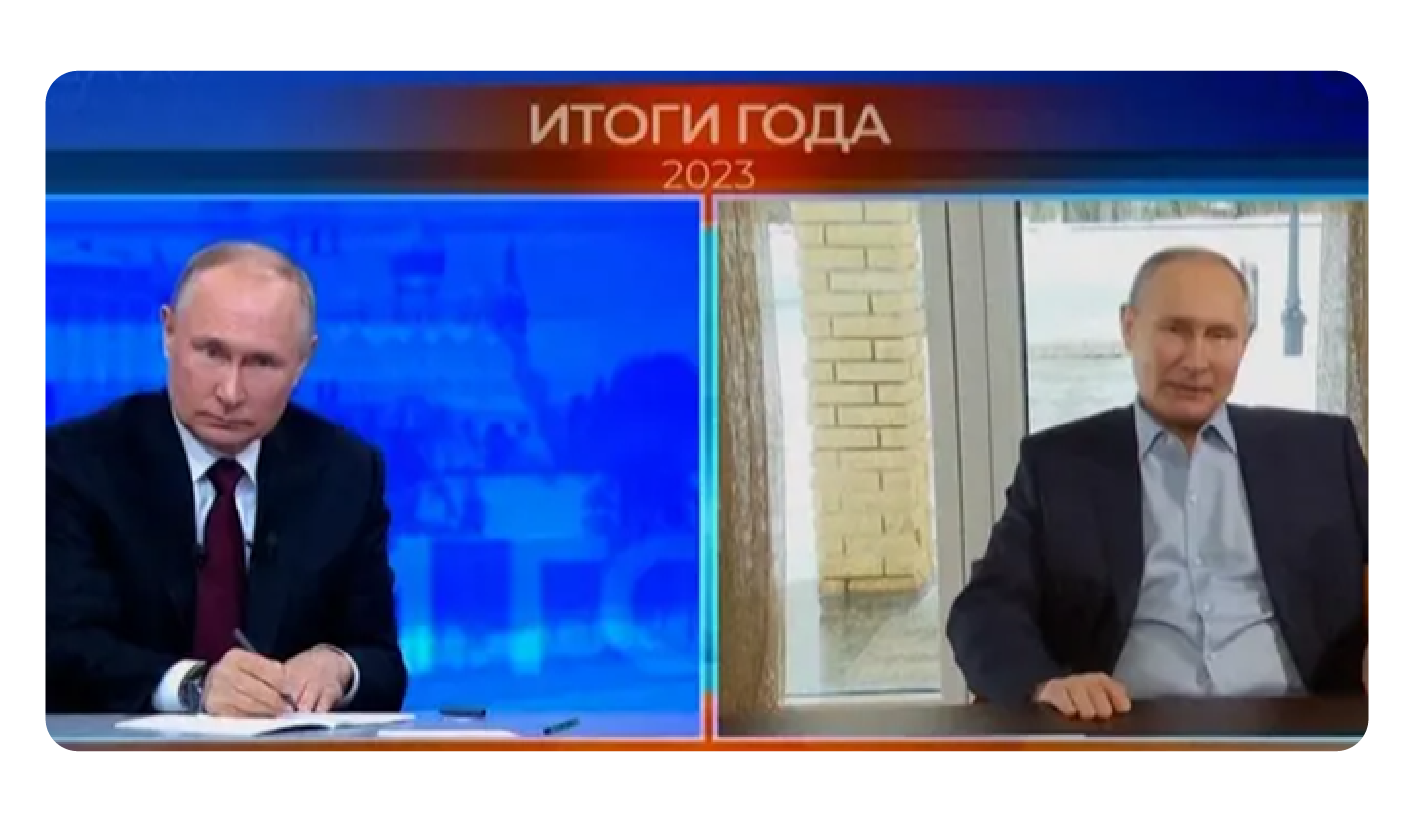 [Left: real, right: AI-double]
[Left: real, right: AI-double]
The AI-double then proceeded to ask his question, “Hello, my name is Vladimir Vladimirovich. I am a student at St. Petersburg State University. I want to ask, is it true you have a lot of doubles?”
Almost a year ago, Joe Rogan, one of the most popular podcasters in the world, was seen selling a men’s health supplement on TikTok. He and Dr. Andrew Huberman were seen promoting this random supplement together.
It turns out the video was mostly original, but Joe’s voice was analyzed, deepfaked, and superimposed on the original video to make it look like he was promoting the supplement.
These were just some of the mild examples of deepfakes on the internet. The rabbit hole goes deeper. From fake war announcements to artificial hate speech to explicit content—deepfakes are a much bigger problem.
Let’s dive deeper.
What is a deepfake?
A deepfake is a sophisticated form of artificial intelligence-driven manipulation, specifically involving creating or altering audio-visual content to present a fabricated or manipulated reality.
This technique employs deep learning algorithms, often utilizing neural networks, to seamlessly blend or replace elements within existing media, such as swapping faces in videos or altering voices with unnerving accuracy.
While initially developed for entertainment purposes, deepfakes have raised significant concerns due to their potential for misuse, ranging from spreading misinformation and malicious propaganda to creating convincing forgeries with serious consequences.
How do deepfakes work?
Let us first understand deep learning and neural networks using a simple example.
Alright, imagine you have a super-intelligent robot friend. Now, this friend is learning to recognize different things, like showing the difference between cats and dogs in pictures. Deep learning is like how your friend gets better at this over time.
Now, think of a neural network as your robot friend's brain. It comprises many tiny parts called neurons, just like our brains. Each neuron helps the robot understand a small amount of what it's seeing, like the shape of an ear or the color of fur on an animal.
Deep learning is like teaching your robot friend by showing it many, many pictures of cats and dogs. Each time it makes a mistake, it learns a bit more about what makes a cat a cat and a dog a dog. The more pictures it sees, the smarter it becomes at telling them apart.
So, deep learning is like your robot friend learning from lots of examples to become really good at recognizing things, and a neural network is the brain that helps it do this. Just like you learn from seeing and doing things, the robot learns from lots of pictures and keeps getting better at figuring out what's what.
Now, imagine your smart robot friend has become even more advanced and can not only recognize things but also create new things that look incredibly real—this is where deepfakes come in.
Deepfakes use a special kind of artificial intelligence called deep learning, similar to what your robot friend uses. Instead of just identifying things, deepfakes go a step further by mimicking and generating new content. They use something called neural networks, which are like layers of filters that analyze and understand information.
For example, in a deepfake video, the neural network analyzes a person's face in different images and videos, learning all the details—like how their eyebrows move, their expressions, and how their lips sync when they talk. Once the neural network has learned these patterns, it can generate a new video of that person saying or doing things they've never actually done.
Think of it as your robot friend being so good at understanding faces and voices that it can create a video that looks and sounds exactly like someone else, even though that person never did or said those things. It's like a super advanced form of digital impersonation.
This technology has both creative and concerning applications. While it can be used for fun and entertainment, like putting a friend's face on a movie character, it also raises serious issues about misinformation and the potential misuse of realistic-looking fake content.
Deepfake applications: How it was meant to be
-
Solving the continuity problem in the entertainment industry.
Deepfakes offer a game-changing tool for the entertainment industry. In 2013, the movie Fast and Furious 7 was in the middle of filming when Paul Walker, a prominent actor in the movie franchise, died in a car crash. In such unfortunate events, instead of changing the remaining part of the movie script, filming can continue based on the original script. The face of the original actor can be superimposed on a body double to shoot the rest of the film.
Dangerous and life-threatening stunt scenes can also be shot without physically risking anyone’s life.
-
Learning new languages and understanding cultural nuances.
Deepfake technology can be harnessed to create realistic language tutorials. Learners can practice with videos of native speakers, improving pronunciation and cultural nuances. This immersive experience can significantly improve language learning and cross-cultural understanding.
-
Learning history through realistic reenactments.
Deepfakes can bring history to life by generating realistic depictions of historical figures delivering speeches or engaging in pivotal events. This visual aid can make history more engaging for students, providing a vivid understanding of key moments in time.
-
Highly customized marketing and advertising.
Deepfakes allow for highly personalized and targeted advertising. Brands could create ads featuring familiar faces tailored to specific demographics, making their campaigns more relatable and impactful.
Salespeople could use tools like Potion to send personalized video messages to thousands of prospective clients without opening the camera app on their phones.
-
Introducing more inclusion and localization in media.
Deepfake technology can be utilized to make media more inclusive. For example, dubbing classic movies or TV shows into various languages with the original actors' faces and expressions intact can improve accessibility for global audiences.
-
Preserving lost voices.
With limited audio recordings, deepfake technology can recreate the voices of historical figures or loved ones who have passed away. This could allow future generations to hear the words and wisdom of influential individuals.
-
Innovations in the gaming and virtual reality space.
Multiple reports by reputed forecasters estimate that the gaming and virtual reality market is expected to cross 1.1 trillion dollars (US) in size before the start of the next decade.
Deepfakes will be a big part of it.
Deepfakes could enhance the gaming experience by creating more realistic and personalized avatars. Gamers could see their faces mapped onto in-game characters, leading to a more immersive and customized virtual reality experience.
Famous people like actors could also be a part of the gaming industry. Cyberpunk 2077, a video game released in 2020, stars actor Keanu Reeves in the cut scenes and is available as a playable character.
-
Restoration in film and television.
Restore old or damaged film footage by using deepfake technology to reconstruct missing scenes or enhance the overall visual quality. This can contribute to the preservation of cinematic history.
In cases of loved ones, apps like MyHeritage go one step further. Their deepfake technology can accurately animate deceased people from old photos—literally bringing them back to life.
-
Special effects in video productions.
The biggest hurdle today, when it comes to special effects, is time. It takes a lot of time to build special effects scenes. It’s a careful balancing act between filming using greenscreens and computer-generated graphics.
Film and television productions, in the future, can leverage deepfakes to create mind-blowing special effects in just a matter of hours or just a few days.
This could streamline the process of bringing fantastical creatures or futuristic elements to the screen with unprecedented realism.
Top 10 tips on how to spot a deepfake video or image
-
Analyze facial inconsistencies. Deepfakes often struggle with maintaining natural facial expressions. Look for inconsistencies in lip sync, blink rate, and facial movements. Real faces have subtle nuances that are challenging for deepfake algorithms to replicate.
-
Check for unnatural gaze. Eye contact is a key indicator. In deepfakes, eyes may appear lifeless or move unnaturally. Pay attention to how well the eyes follow movements and if the gaze aligns naturally with the rest of the face.
-
Examine hair and clothing details. Deepfakes may have difficulties with intricate details like hair strands or clothing textures. Zoom in on these areas to spot irregularities, such as fuzzy outlines or unrealistic movements. It is also widely known that most AI algorithms cannot (yet) properly replicate human hands or fingers. Pay close attention to those.
-
Evaluate lighting and shadows. Lighting inconsistencies can betray a deepfake. Pay attention to shadows, reflections, and how well the subject blends with the background. Deepfakes may struggle to replicate realistic lighting conditions.
-
Listen for audio anomalies. Deepfake technology is advancing, but audio remains a challenging aspect. Check for any discrepancies in voice tone, pitch, or sudden changes in audio quality. Deepfakes might exhibit such artifacts or unnatural pauses in speech.
-
Scrutinize unusual backgrounds. Deepfakes may struggle with background elements. Look for unnatural movements, distortions, or inconsistencies in the surroundings. Deepfake algorithms often have difficulties generating realistic backgrounds.
-
Verify the source and context. Deepfakes can be spread through various channels. Always cross-verify the source and context of the content. Authentic videos often have consistent information across different platforms.
-
Fight fire with fire. Use specialized tools designed to detect deepfakes. Platforms like Deepware Scanner or Microsoft's Video Authenticator employ advanced algorithms to identify inconsistencies in facial features and movements.
-
Understand the limitations of deepfake technology. Stay informed about the current capabilities and limitations of deepfake technology. Recognizing that deepfakes might not be flawless helps you approach content with a critical eye.
-
Educate yourself continuously. The field of artificial intelligence, machine learning, deep learning, and neural networks is moving at breakneck speeds. Stay updated on the latest advancements, detection techniques, and emerging trends to refine your ability to spot deepfakes effectively.
Industry giants unite against the deepfake problem
Big players in the camera world – Nikon, Sony, and Canon – are teaming up to tackle the growing threat of deepfake images.
They're rolling out cutting-edge tech that embeds digital signatures right into their cameras.
It's not just a fancy feature; it's a powerful move to authenticate images, proving they're legit and untampered.
These digital signatures pack in key details like when, where, and who took the photo. Combine these key details with powerful encryption, and they make it nearly impossible to tamper with the contents of the photo.
This is a game-changer, especially for professionals like photojournalists who live and die by the trustworthiness of their work.
Here's the breakdown: Nikon is putting this game-changing feature in their mirrorless cameras, while Sony and Canon are slotting it into their top-notch mirrorless SLR cameras. They've even agreed on a global standard for these digital signatures, making sure it is compatible with a web tool called "Verify."
Now, Verify isn't some random thing. It's a tool launched by a gang of heavy hitters – global news groups, tech giants, and camera whizzes.
And get this – it's free!
Users can double-check if an image is the real deal by looking at its digital signature. If it has one, Verify will give a thumbs-up to its authenticity.
If AI had a hand in creating or editing the image, Verify tags it as having "No Content Credentials."
Why the rush for this tech? Well, deepfake content is blowing up, with tweaked images of big shots like ex-US President Donald Trump, Japanese Prime Minister Fumio Kishida, and Indian Prime Minister Narendra Modi making the rounds.
Expected to hit the market in 2024, Sony is taking the lead with a spring release, followed by Canon later this year.
The good news is that these giants are not stopping at photos – Sony's eyeing video authentication, while Canon's building something similar for videos.
These companies have even put their tech to the test with reputed news organizations like The Associated Press.
But it's not just the camera crowd in this fight.
Google's got an invisible digital watermark tool to spot AI-made pics, Intel's tech checks skin color changes for authenticity, and Hitachi's on the scene, too, sniffing out online identity fraud.
This united front against deepfakes shows that industry bigwigs are dead serious about bringing back trust in the images shaping our view of the world.
Gaps in legal regulation and fixes
Deepfake tech is turning heads, but it's also raising eyebrows due to a lack of solid rules.
Let's take a closer look at the gaps in regulations surrounding this tech marvel and why they matter.
-
A big challenge is figuring out exactly what counts as a deepfake. The current rules struggle to keep up with the fast changes in this tech. Is it harmless fun or a tricky attempt to fool someone? Getting a clear definition is the first big step in making rules that work.
-
Deepfake content doesn't stick to one place; it travels the world online. This makes it tough for rule-makers to control it effectively. We need a set of international rules that everyone agrees on to fill in the gaps and fight against the misuse of deepfake tech together.
-
Rules need to keep up with how fast deepfake tech is evolving. As soon as we make rules for one thing, creators find new ways to use the tech. To tackle this, rule-makers and tech experts need to team up and stay one step ahead of those using the tech for bad stuff.
-
Privacy is a big worry with deepfake tech, especially when it comes to getting permission. Current rules don't do a great job of dealing with the ethical questions about making and spreading deepfakes. We need rules that find the right balance between creative freedom and protecting people from their faces being used without permission.
-
Deepfake tech can mess with politics, from changing speeches to faking video evidence. This adds a new layer of worry. Making rules that keep our politics honest without stopping free speech is a tough challenge.
A few examples of government efforts to fix the deepfake problem
United States: Rep. Yvette Clarke introduced the DEEPFAKES Accountability Act, which aims to protect individuals from being misrepresented by certain kinds of digital content and requires creators to label all deepfakes uploaded to online platforms.
China: The Cyberspace Administration of China implemented regulations requiring all deepfakes to be prominently labeled, explaining that deepfakes create risks of endangering national security, undermining social stability, disrupting social order, and infringing on the legitimate rights and interests of others.
South Korea: In 2019, South Korea made it a criminal offense to publish deepfake videos created with artificial intelligence, with the law taking effect on January 1, 2020.
European Union: The EU has been working on addressing deepfakes through various initiatives, including the development of detection technology and the establishment of a baseline for prosecutors, regulators, and victims to stand up against the threat posed by deepfakes.
Brazil: Brazil has introduced legislation to regulate deepfakes, with the bill focusing on two primary concerns: interfering with elections and developing explicit content.
Impact of deepfakes on society
The impact of these sophisticated yet deceptive creations is far-reaching.
On the one hand, they offer entertainment value, enabling seamless face-swaps in videos or placing familiar faces into unexpected scenarios.
However, the darker side emerges as deepfakes become a potential tool for misinformation and manipulation. The ease with which one can now alter the very fabric of reality raises concerns about trust and authenticity in the already complex world that we live in.
Imagine a world where anyone can be made to say or do anything on screen, blurring the line between truth and fiction. This erosion of trust extends beyond personal relationships to public figures and institutions, as even the most convincing videos can be manufactured with relative ease, as we saw at the beginning of this article.
The implications for politics, journalism, and online discourse are profound, with the potential to disrupt democratic processes and sow discord.
As deepfake technology advances, the challenges in detecting these synthetic creations grow. The impact is not limited to the digital realm; real-world consequences can unfold when false narratives gain traction. Innocent individuals might find themselves implicated in events they never participated in, while the guilty may exploit deepfakes to evade accountability.
The legal and ethical dimensions of this technology are still in their infancy, and society grapples with how to add clarity to the blurry lines between freedom of expression and the potential harm caused by manipulated content.
Most importantly, deepfakes introduce a psychological element, shaking the foundations of personal identity and trust.
As we witness the malleability of digital representations of ourselves and others, questions about the authenticity of our online experiences become unavoidable. In an era where visual evidence once held a certain level of irrefutability, the rise of deepfakes prompts us to approach information with a heightened sense of skepticism.
This, in turn, may reshape how we engage with digital media, forcing us to critically evaluate the legitimacy of what we see and hear.
Conclusion: A game of cat and mouse
At the end of the day, solving the deepfake problem is a never-ending game of cat and mouse.
Bad actors will keep finding newer ways to evade the law and regulators, and big companies will keep building “lawful fences” around us to keep the cat inside.
But no matter what happens, this technology is being developed at a rapid pace.
So, is there a revolution on the horizon?
Only time will tell.
Don’t let anyone deepfake your documents
Hope you enjoyed this comprehensive article about deepfakes. Before you click off, we would like to tell you that, just like your identity, we at DrySign also work very hard to secure your documents from tampering, theft, and loss. Learn more
Sources: google.com | en.wikipedia.org | reddit.com | linkedin.com | x.com | youtube.com | theguardian.com | bing.com | msn.com | bbc.com | dw.com | en.kremlin.ru | grandviewresearch.com | myheritage.com | bolnews.com | sendpotion.com | quinnemanuel.com
DISCLAIMER: The information on this site is for general information purposes only and is not intended to serve as legal advice. Laws governing the subject matter may change quickly and Exela cannot guarantee that all the information on this site is current or correct. Should you have specific legal questions about any of the information on this site, you should consult with a licensed attorney in your area.











